SafetyDetective’s research lab discovered a leak online regarding the Ethiopian National Security Agency (INSA).
The hackers managed to easily scrape a few hundred of INSA agents’ email addresses and passwords, allowing them to potentially log in to INSA’s email server (and personal emails using the same credentials).
INSA notoriously monitors and intercepts all Ethiopian citizens’ communication, in an attempt to ‘safeguard the country’s information and information structures’, according to their website’s mission statement…
Political hacking is nothing new: While the fact that hackers could so easily hack a security agency – and the Ethiopian INSA especially – is alarming, what was even worse was that the passwords we discovered in use by INSA were basic (and hackable) beyond belief. Basically, they weren’t salted and hashed. While big databases usually have their data protected and encrypted (in case someone breaks in), this one didn’t and had common passwords easy to decrypt.
Just take a look for yourself:
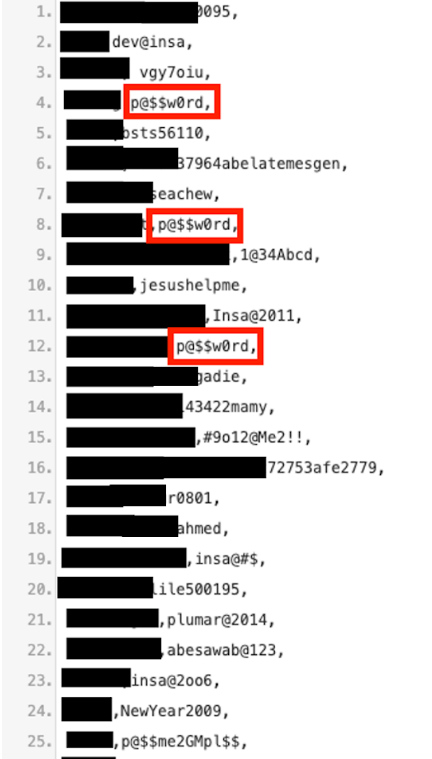
Screenshot of 42 of the 300 secure email addresses and passwords of Ethiopian INSA employees
Of the 42 passwords screenshotted above (of 300 overall), 9 of those are ‘p@$$w0rd’ – AKA, one-step above ‘password’ which we also saw 3 uses of in total (of 300). That’s really secure, security agents!
In fact, out of the 300 agent email addresses we scraped, we counted 142 uses of ‘p@$$w0rd’ (that’s almost half), and 62 passwords containing a `123’ sequence, similar to another surprising set of unchanged default passwords that were discovered by our team. It goes without saying that, even had the server not been hacked, the passwords we saw post-scraping were easily hackable.
As the most tech-savvy people in Ethiopia, whose entire careers literally revolve around online and national security, their lack of secure passwords is absolutely shocking, although major security breaches affecting ordinary citizens are nothing new.
That and the fact that, when we tried to verify the hack, we were able to use these leaked login credentials again and again.
Since the data was scraped a while ago, it now seems that these credentials no longer work, meaning INSA has either reset these passwords or changed the internal email server.
But, sensitive INSA data is still available to even the most low-level of hackers: taking the leaked usernames and using a brute-force attack on the new email server would still easily hack agents’ new passwords especially if they are as insecure and hackable as they were previously.
We suggest the agents set new, stronger passwords that are as secure as their employment requires them to be: Safety Detective’s Password Checker will allow INSA agents to strengthen their preferred passwords (other than ‘p@$$w0rd’) to prevent any further hacks.
It is recommended that databases encrypt sensitive info, then if the worst happens, attackers will be left with useless hashes.
Because all matters of national security deserve to be securely ‘p@$$w0rd’ protected.
SD






































